AWS Lambda
Connect Sentry to your AWS account to automatically add Sentry error and performance monitoring to your Node/Python Lambda functions.
Install
Sentry owner, manager, or admin permissions are required to install this integration.
Navigate to Settings > Integrations > AWS Lambda.
Press Add Installation to open the installation modal.
Select the project for your Lambda integration. Note: This project cannot be changed after installation is complete. If you only have a single project, you'll skip this step.
Click Go To AWS.
Scroll to the bottom of the Create Stack page, check the box, then press Create Stack to create a CloudFormation stack in your current region. This stack allows Sentry to automatically instrument your Lambda functions.
Wait for the stack to be created, which is confirmed by seeing the status change to Create Complete, then click I've created the stack.
Now copy your AWS account number, select the region you want to use, and press Next.
You need to create the CloudFormation stack only once per account, even when installing the integration in multiple regions. If you are setting up the integration in a second region, copy the externalId from the existing CloudFormation stack on the "Parameters" tab into the form shown above.
Select the Lambda functions to automatically add the Sentry layer and necessary environment variables when you Finish Setup. Note: You can enable or disable Sentry on Lambda functions after installation.
Wait a few minutes as the Lambda functions are enabled. If any functions failed to instrument, follow the suggestions in Troubleshooting.
Troubleshooting
If you need help solving issues with your Sentry AWS Lamba integration integration, you can read the edge cases documented here. If you need additional help, you can ask on GitHub. Customers on a paid plan may also contact support.
Error SentryRole already exists
The stack already exists on your account; you can proceed to the next step of adding your AWS account information.
Error Invalid existing layer
Your Lambda function has a layer that no longer exists. Please remove the problematic layer, then enable Sentry on the Lambda in the configuration view for the integration.
Error Please validate the CloudFormation stack was created successfully
Sentry is unable to access your AWS account through your CloudFormation stack. This means either the stack has not been created or the external ID used doesn't match the one in your installation. You can go to the Parameters tab of the CloudFormation stack to copy the value of the external ID and paste it into the form field.
Error Invalid role associated with the lambda function
The role associated with your lambda function no longer exists. Please add a new role to your lambda function, then enable Sentry on the Lambda in the configuration view for the integration.
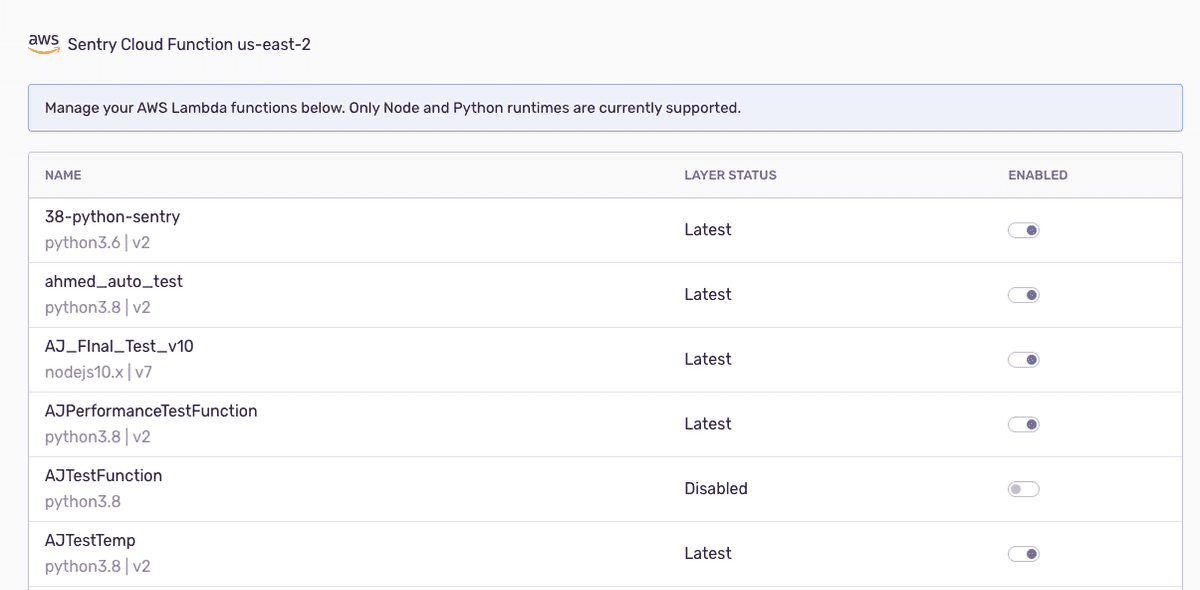
Configure
The integration configuration view allows you to do the following with your Lambda functions:
- Enable Sentry
- Disable Sentry
- Update the Sentry Lambda Layer to the latest version
In the table view, you will also see the version of the Lambda layer below the name.
Remove Installation
Note that when the integration is uninstalled, your Lambda functions will still be instrumented with Sentry and you will continue to receive errors. If you want to disable Sentry for all your Lambda functions, you should disable Sentry for each function before uninstalling. Note, you can also uninstall and then reinstall if you would like to change the Sentry project for your Lambdas.
Learn more about how this integration works.
Serverless Framework
Note that this integration will configure your existing lambda functions correctly to use the SDK layer and set the appropriate environment variables as per how this integration works. You can check the output aws lambda get-function-configuration --function-name <yourFunctionName> and this works.
However when you perform a subsequent sls deploy the environment variables are not maintained but it appears the reference to the layer is retained. A workaround exists where you can set the layer definition and environment variables in serverless.yml. There are two problems with this, you have to manually add the reference to the SDK layer for every function you want "Sentrified" and you can't maintain the latest layer version automatically.
Node
# other configuration
provider:
# more configuration
region: <AWS_REGION>
environment:
SENTRY_TRACES_SAMPLE_RATE: '1.0'
SENTRY_DSN: '<SENTRY_DSN>'
NODE_OPTIONS: '-r @sentry/serverless/dist/awslambda-auto'
custom:
layers:
- arn:aws:lambda:${self:provider.region}:943013980633:layer:SentryNodeServerlessSDK:26
# - arn:aws:lambda:${self:provider.region}:943013980633:layer:SentryNodeServerlessSDK:latest
functions:
<yourFunctionName>:
handler: <yourLambdaHandlerFunctionPath>
layers: ${self:custom.layers}Python
# other configuration
provider:
# more configuration
region: <AWS_REGION>
environment:
SENTRY_TRACES_SAMPLE_RATE: '1.0'
SENTRY_DSN: '<SENTRY_DSN>'
custom:
layers:
- arn:aws:lambda:${self:provider.region}:943013980633:layer:SentryPythonServerlessSDK:6
# - arn:aws:lambda:${self:provider.region:943013980633:layer:SentryPythonServerlessSDK:latest
functions:
<yourFunctionName>:
handler: sentry_sdk.integrations.init_serverless_sdk.sentry_lambda_handler
environment:
SENTRY_INITIAL_HANDLER: '<yourLambdaHandlerFunctionPath>'
layers: ${self:custom.layers}Currently there is no way of using the latest layer plugin since the lambda:ListLayerVersions on resource: arn:aws:lambda:eu-west-1:943013980633:layer:SentryNodeServerlessSDK has not been given the necessary permissions.
It is a relatively new integration but there is definitely a case to write a serverless plugin to make this super-smooth. There is an older version but it requires code changes to the handler and doesn't use NODE_OPTIONS. A new plugin could also add the Sentry layer to every function automatically.
SST
To use this integration with Node functions in SST, you'll need to:
- Import the Lambda layer using the
LayerVersionconstruct and set it by callingaddDefaultFunctionLayers. - Then set the
NODE_OPTIONS,SENTRY_DSN, andSENTRY_TRACES_SAMPLE_RATEenvironment variables with theaddDefaultFunctionEnvmethod.
You can read more about this over on the SST docs.
Our documentation is open source and available on GitHub. Your contributions are welcome, whether fixing a typo (drat!) to suggesting an update ("yeah, this would be better").